How to Spot a Phishing email
Cybercriminals know that the weakest part of your cybersecurity is your employees. In fact, according to a study conducted in 2021, 84-88% of all data breaches are caused by an employee's mistake.
Phishing, once primarily targeting the consumer market, has evolved, becoming the leading social attack on companies and the primary cause of most security breaches. Before we explore how to identify signs of a phishing email, let's first understand what these fraudulent emails are and how they operate.
Understanding Phishing: How to Identify Suspicious Emails
What is phishing?
Phishing is a type of social engineering attack frequently employed to steal personal details such as account numbers, credit card information, phone numbers or passwords. This deceptive tactic occurs when a threat actor impersonates a trusted entity, convincing you to open an email, instant message, or text message. Once opened, you may unwittingly click on a link, leading to the installation of malware and the potential theft of sensitive data.
Phishing is not a new concept, but its methods have become increasingly sophisticated over time. It's crucial to understand the various forms phishing can take, including email, instant messaging, and text messages. In addition to stealing personal details, phishing attacks can also lead to financial fraud, identity theft, and even the compromise of entire networks. Providing examples of recent high-profile phishing attacks or statistics on the rise of phishing attempts globally could emphasize the severity of the threat.
Social engineering attacks involve threat actors studying your social media accounts to gather personal information about you and your connections. They then use this information to manipulate and deceive users into making security mistakes or divulging sensitive information.
It’s time to fortify your defences and prepare for the worst-case scenario. Watch our webinar on Backup & Disaster Recovery – the art of business continuity and rapid recovery after a security incident.
Common Indicators of a Phishing Attempt
Identifying signs of a phishing email involves recognising several key indicators.
Here are our top 8 red flags:
1. The from address is misspelt or from a freemail account.
Don’t just check the name of the person sending you the email. Instead, check their email address by hovering your mouse over the ‘from’ address. Unless cybercriminals have compromised the organisation’s email systems, they’ll have to use a different domain. This usually involves a public email domain, such as Gmail, wherein the message will come from an address that looks like, for example, ‘netitude@gmail.com’.
Always inspect the email address closely, and make sure there are no spelling mistakes or alterations made in the email address, such as additional numbers or letters. For example, here it’s our domain, but with an extra T – at a glance, you probably wouldn’t spot this!
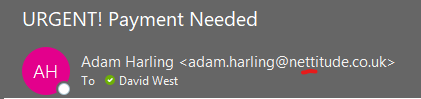
2. The email insists on urgent action.
Urgency tactics are a hallmark of phishing scams, exploiting fear or anxiety to prompt immediate response. Be suspicious of emails that claim you must click on a link, call an unknown number, or open an attachment immediately.
Creating a false sense of urgency is a common trick of phishing scams to gain sensitive information. Often, they’ll claim you have to act now to claim a reward or avoid a penalty.
3. The content seems out of character for the sender.
If you’ve received what looks like a legitimate email from a colleague that seems out of character, take a moment to ask yourself, “would this person really contact me about this?”
Hackers now have access to an abundance of information at their fingertips due to the proliferation of technological devices, social media channels, and, of course, the internet. All it will take is some sub-par privacy settings to get you in a whole host of trouble, with personal details and contacts able to be nabbed and leveraged within seconds.
Therefore, if you receive a dodgy message from the sender that seems out of character, we urge you to speak to that person over the phone or, if possible, face-to-face. If you reply to the email itself, there’s a good chance the attacker already has control of their mailbox and could respond to confirm the initial request.
4. An impersonal greeting is used.
Fraudsters often send thousands of phishing emails at once; they may have your email address but not your name. So, an impersonal message could spell a mass-scale phishing campaign.
Be sceptical of an email sent with a generic greeting such as “Dear Customer” or “Dear Member”.
5. The email contains spelling or grammatical mistakes.
Spelling and grammar can play a significant role in detecting a phishing message. Check for fonts that don’t match the brand, spelling, and grammatical errors. An email from a legitimate organisation should be well-written.
Believe it or not, hackers send error-ridden emails to weed out individuals who may be less observant or unable to recognise mistakes, making them easier targets.
6. Check URLs from suspicious-looking emails.
Don’t open links if you suspect an email message is a scam. Instead, hover your mouse over the link to see if the address matches the link typed in the message. You can also test links by typing them into a URL checker.
7. The email directs to a fake website.
Fraudsters often include a link to a malicious website that displays a sign-in page to trick you into disclosing your login credentials. Be careful; just because a site consists of a company’s logo or looks real doesn’t mean it is.
Check the web addresses carefully, for example, www.netitude.co.uk or www.netittude.co.uk. If in doubt, exit the website.
8. The email includes a strange or unexpected attachment.
Unsolicited emails that contain attachments reek of hackers. Typically, authentic institutions don’t randomly send emails with attachments but instead, direct you to download documents or files on their website.
Sometimes, companies that already have your email will send you information, such as a white paper that may require a download. Look for high-risk attachment file types, including .exe, .scr, and .zip.
Contact the company directly using contact information obtained from their website when in doubt.
How to prevent phishing attacks
Effective protection against phishing attacks requires collaboration between users and enterprises.
For users, vigilance is vital. For enterprises, taking specific measures can mitigate both phishing and spear-phishing attacks:
- Implement Two-Factor Authentication (2FA) to add an extra layer of verification.
- Enforce strict password management policies within the organisation.
- Conduct regular educational campaigns to promote secure practices, such as avoiding clicking on external email links.
Technology is a double-edged sword in many ways; it's used by cyber attackers to steal information and attack weaknesses in our cyber security, whilst it also acts as the shield that protects us from a constant barrage of malware and phishing emails.
We cannot stress the importance of keeping software and systems up-to-date to patch vulnerabilities exploited by phishing attacks. Failing to do so could result in severe consequences such as reputational damage and quite considerable cost.
Corey Nachreiner, CTO of WatchGuard, suggests, "Your phishing education program isn't complete until you phish your own company's tank." This involves sending realistic but fake phishing emails to test users and then designing a training program based on the interactions.
Tools like KnowBe4’s free phishing test enable you to simulate phishing scenarios for your users, allowing you to tailor training programs effectively.
Our Managed IT Service packages include security awareness training and a range of industry-leading cybersecurity solutions. To learn more about our IT support services, reach
If you’d like to learn more about our IT support services, get in touch or book a meeting. We’d love to talk about how we can support your business security!


In essence, phishing remains a persistent and evolving threat in the digital landscape, leveraging deception to exploit vulnerabilities and compromise sensitive information. Recognising the signs of a phishing attempt is paramount to safeguarding personal and organisational security.
At Netitude, we're committed to empowering businesses with the knowledge and resources needed to navigate the complex landscape of cybersecurity. Through our Managed IT Service packages and industry-leading solutions, we offer comprehensive protection against phishing and other cyber threats. Reach out to our friendly team of experts today to learn more about how we can support your business security needs and ensure peace of mind in an increasingly digital world.